For customers who use Okta and are looking are for an easy and secure way to onboard clients onto their network, Aruba Central just released a brand new integration. The Cloud Auth feature within Aruba Central now directly integrates with Okta Workforce Identity Cloud and allows users to seamlessly connect to their wired and wireless networks.
Before you Begin
Please review the Cloud Auth configuration overview: https://www.arubanetworks.com/techdocs/central/2.5.8/content/nms/policy/config-cda-in-okta.htm?Highlight=okta
Steps to Configure Okta Workforce Identity Cloud as an Identity Provider
Step 1: Create the Okta Cloud Auth OIDC Application
Step 2: Create the Okta Cloud Auth API Service
Step 3: Configure the Aruba Central Cloud Auth Service
Step 4: Validate and Test
Create the Okta Cloud Auth OIDC Application
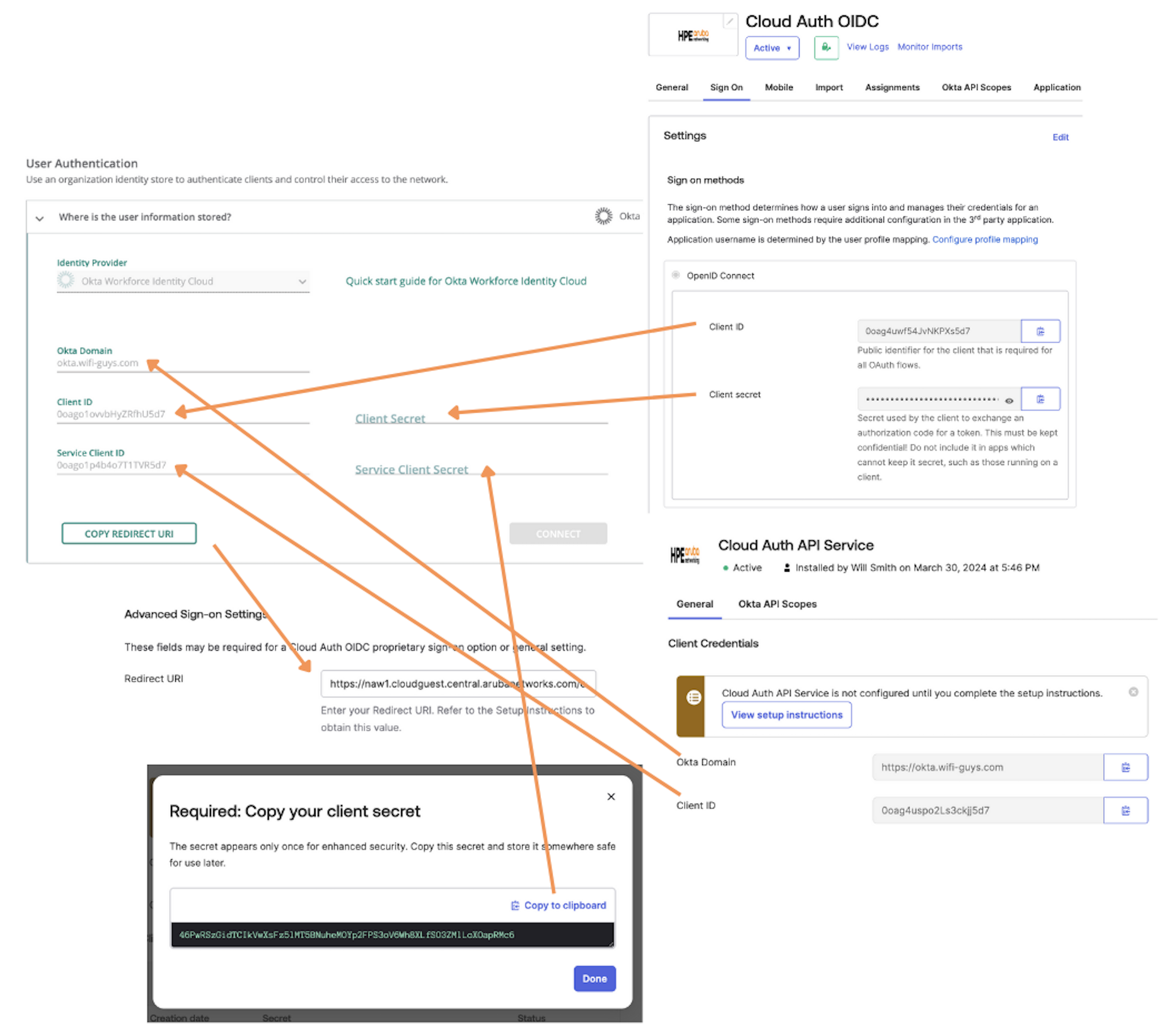
Log into the Okta management portal and under Applications click Browse App Catalog
Search for “Cloud Auth OIDC” and click Add Integration.
Once the application is installed Select Sign On > Edit > then Scroll down to the Advanced Sign-on Settings.
Copy the Redirect URI obtained from the user access policy and paste it in the Redirect URI field which is located above the help text. For more information, see Copy Redirect URI.
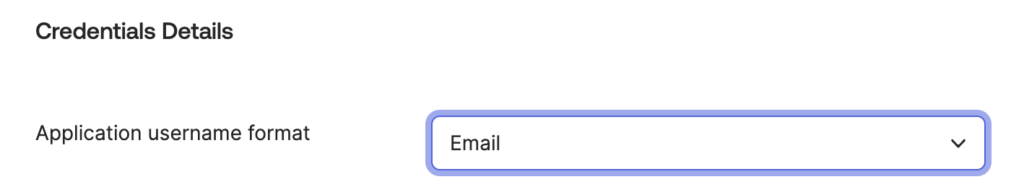
In the Credentials Details section, for Application username format, select Email.
Click Save.
Create the Okta Cloud Auth API Service
Log in to the Okta Workforce Identity Cloud administration console and under Applications Click Browse App Catalog.
Search for Cloud Auth API Service and Select Add Integration.
Select Install & Authorize and Copy this as the Service Client Secret.
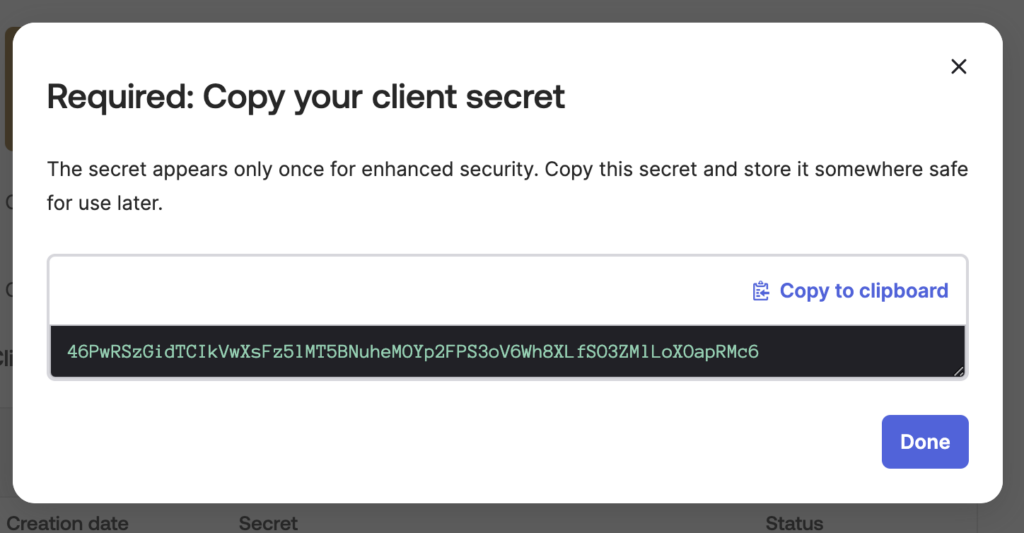
Click Done.
Configure the Aruba Central Cloud Auth Service
Log into Aruba Central as an Admin.
Under the Global view select Security then Authentication & Policy and click Config.
Under User Access Policy click Edit and under identity providers select Okta Workforce Identity Cloud.
Fill in the following fields referencing the values from the Okta ODIC and API applications:
Create the Okta Group to Aruba Client Role Mapping:
At least one mapping must be added. Use the ‘Unspecified’ user group if no other role mappings are needed
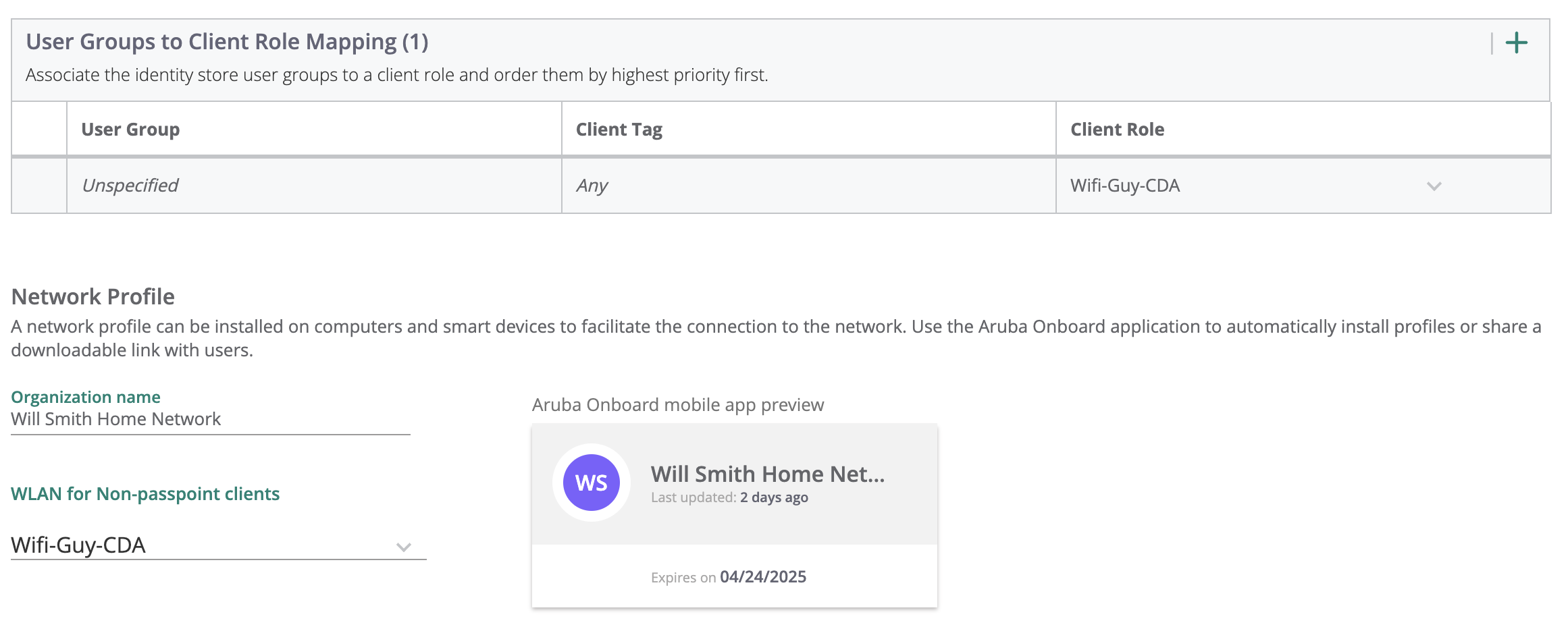
Click Save
Onboard Client – Test and Validate
Under the User Access Policy – Click Copy URL or Open
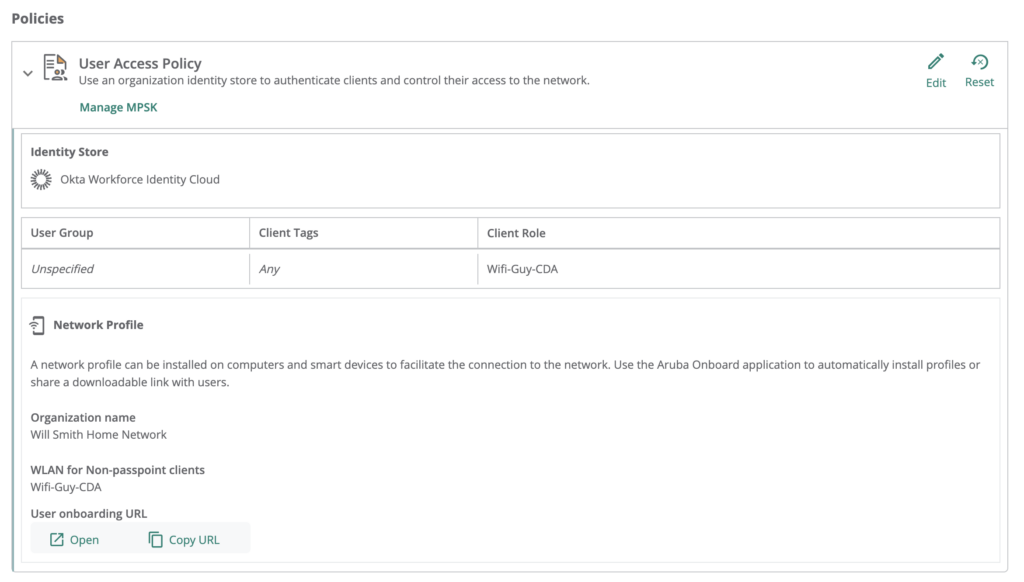
Follow the prompts to install the Aruba Onboard App.
Once the app is installed, it will redirect you to Okta for Authentication.
After successfully authenticating, a unique client cert and profile will be downloaded onto the device.
Verify the client is able to connect to the Cloud Auth enabled SSID.
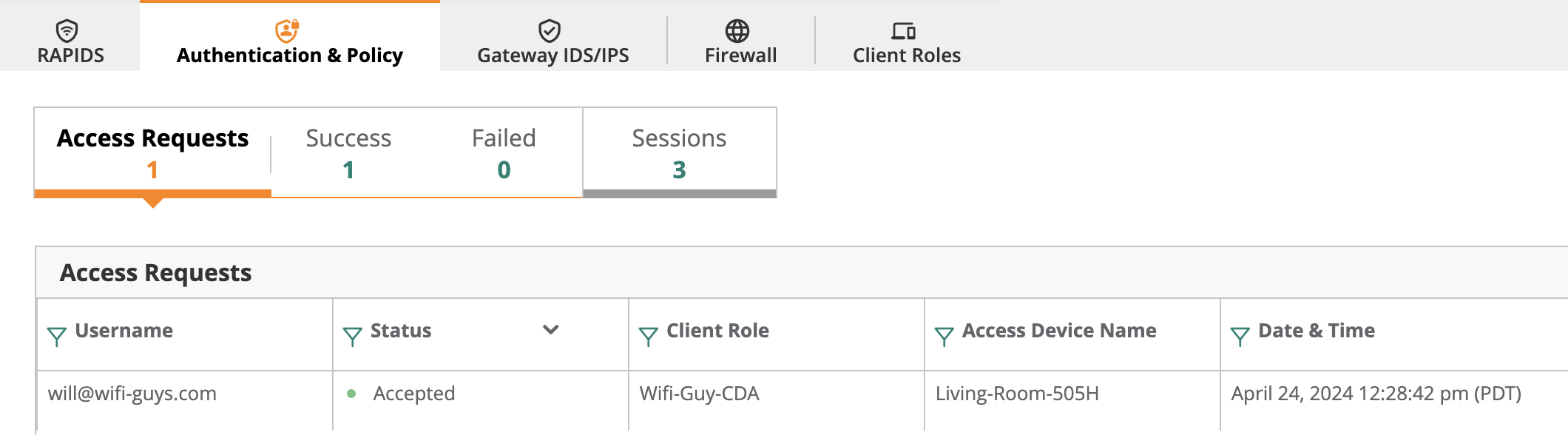
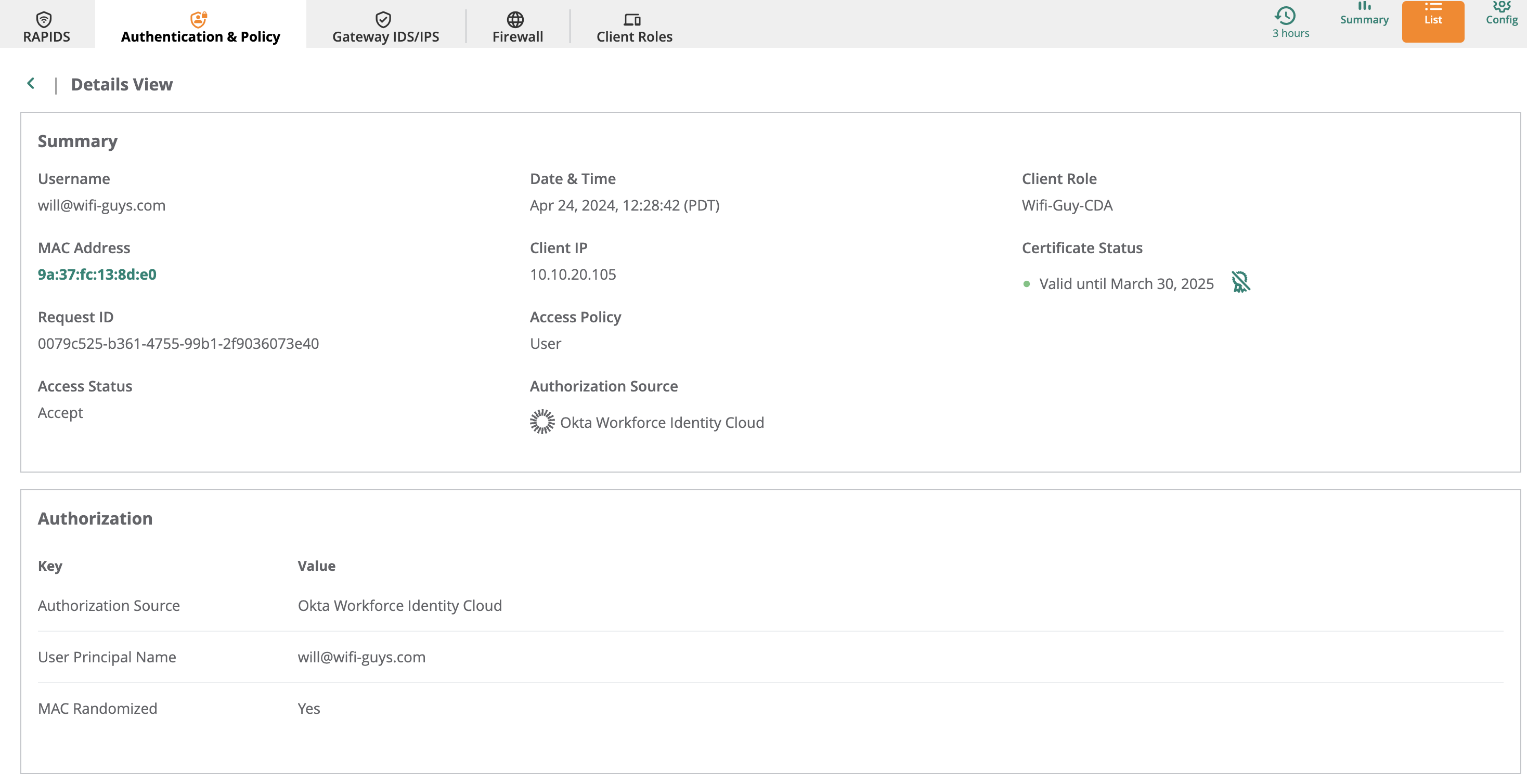
Check the Cloud Auth logs to see authenticiation information and troubleshoot any issues.